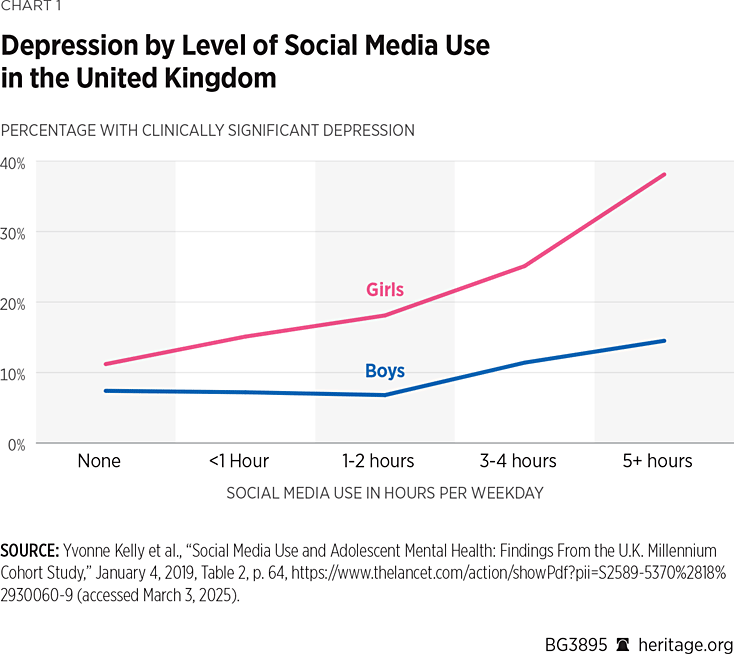
Social science demonstrates that pornography and social media negatively affect the mental health, emotional well-being, and physical behavior of kids. Eighth-graders who spend 10 hours or more per week (1.4 hours a day) on social media are 56 percent more likely to report being unhappy.REF Another survey finds that teens who spend over three hours a day on social media face twice the risk of poor mental health outcomes.REF The average amount of time spent on social media by eighth-graders is over four hours per day.REF
Roughly 80 percent of kids between the ages of 12 and 17 have come across online pornography, and over 50 percent seek it out. Frequent exposure to pornography at a young age cultivates unhealthy views of sexuality and an inclination toward violent behavior.REF Public discourse, news articles, books, congressional hearings, and anecdotal evidence substantiates the message of these statistics.
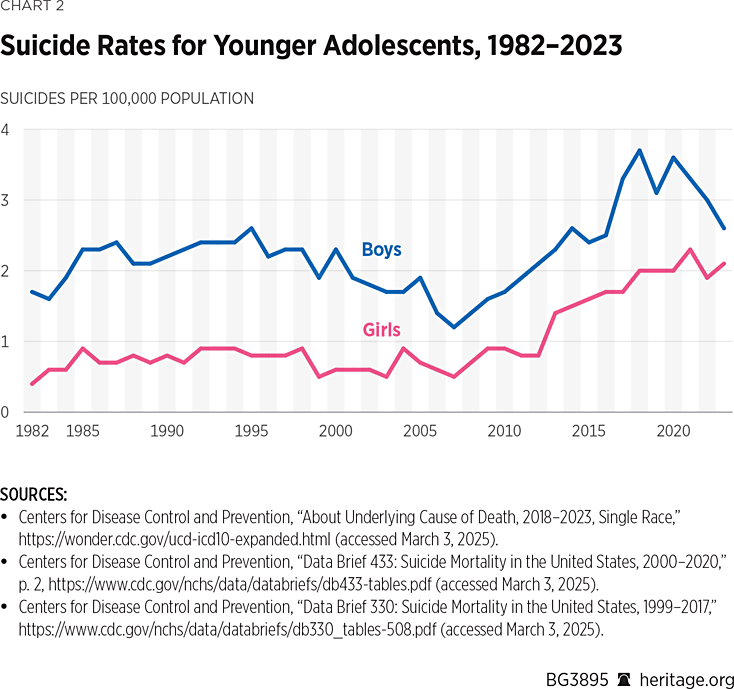
The U.S. needs to do more to protect kids from these online harms. In the worst cases, data shows a significant rise in suicide rates among pre-teens and teens since 2011. At minimum, this suggests a correlation to the rise in smartphone and social media use.REF Despite widespread recognition that kids face serious problems with social media and pornography use, many people dispute the drivers of the problems and, more importantly, how these harms need to be addressed.
The Results of Unfettered Access
A significant cause for these problems is the unfettered access kids have to content and experiences in the digital world from which they are restricted in the real world. Imagine the following scenario in which a child faces no restrictions in the physical world:
Walking down the Las Vegas Strip, 12-year-old Caleb walks into a casino, where he plops down at a slot machine. A waiter offers him an alcoholic beverage, which he eagerly accepts. After a couple hours of gambling and drinking, he stumbles outside and takes refuge in an adult movie theater where he watches an X-rated movie. He feels lonely and empty, but his curiosity leads him on, and he thinks maybe the next spectacle will cheer him up.
The idea that Caleb would be able to partake in any of these experiences at his age is ridiculous and only possible if no one did his or her job and no bystander intervened. Yet Caleb’s experience is one many young children and teenagers encounter online on a daily basis.
Monitoring screen time and using device filters helps shield children from viewing online content not suitable for their ages. However, monitoring screen time does not prevent children from coming across inappropriate content or websites, and filters can be both underinclusive and overinclusive. Furthermore, these strategies do not shield kids from the addictive design features embedded in many platforms. Similarly, parents’ delay of providing personal devices to kids certainly limits their access to and use of social media and pornography, but it does not eliminate all opportunities. In real life Caleb would be stopped by staff, law enforcement, and possibly concerned strangers due to his young age and the legal restrictions placed on minors. It is time to employ similar safeguards online. The most analogous mechanism that consistently prevents children from accessing platforms that harm them is age verification.
Underscoring Online Harms
What separates the problem of social media and online pornography from past concerns of the influence of radio, rock ’n’ roll, television, and magazines on youth is the prolific access to these platforms on smartphones and the addictive design features embedded in the apps. Pornhub’s 2023 Year in Review showed that over 91 percent of its traffic came from mobile devices, up from 49 percent in 2013.REF In 2011, 23 percent of teens had a smartphone, but by 2023, 95 percent had one.REF The ease of accessing porn on smartphones makes it far too dangerous for kids, who have notoriously poor impulse control.
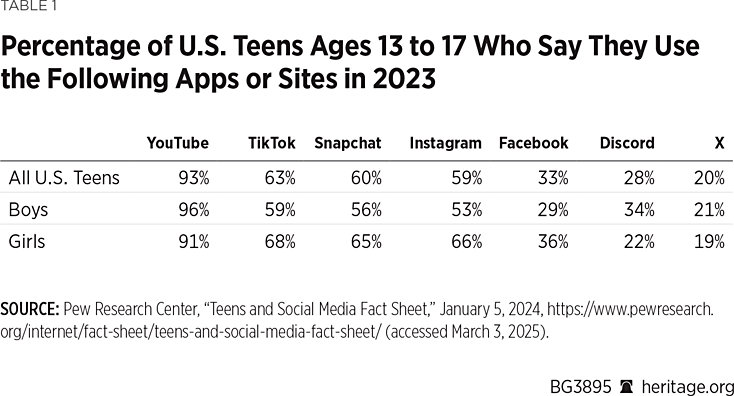
Further, in 2023, Pew Research Center found that 46 percent of teens said they were online almost constantly. This increased from 24 percent in 2015, the first year Pew measured this metric.REF Heavy phone use exacerbates mental, emotional, and behavioral problems in kids. Studies show a correlation between screen time and higher rates of obsessive-compulsive disorders and an impairment of kids’ abilities to self-soothe.REF Push notifications activate dopamine-driven feedback loops causing dependence and even addiction to smartphones.
Children and teens are particularly susceptible to these problems because of their developmental stage. Individuals between the ages of 10 and 19 undergo a highly sensitive period of brain development, more easily succumb to peer pressure, and exhibit the highest risk-taking behaviors of any age group. As stated in a 2023 U.S. Surgeon’s General report:
Frequent social media use may be associated with distinct changes in the developing brain in the amygdala (important for emotional learning and behavior) and the prefrontal cortex (important for impulse control, emotional regulation, and moderating social behavior), and could increase sensitivity to social rewards and punishments.REF
In other words, heavy social media use is rewiring the brains of kids.
Social media companies claim their platforms have great benefits such as facilitating online connection with peers. This is how social media started, and many people enjoyed communicating with friends, uploading digital photo albums, and viewing their friends’ photos. However, research shows that people are posting less on social media and instead are passively consuming content from strangers as a form of entertainment. Users are more self-conscious about what they post, in part because of concerns with perception and insecurities.REF
Kids who decreased or stopped social media use experienced an improvement in mental health, grades, learning, behavioral health, relationships, discipline, and focus. A trial among teens and young adults found that deactivating a social media account for four weeks improved self-reported happiness, life satisfaction, anxiety, and depression.REF Age verification will enforce age restrictions and greatly reduce children’s exposure to these platforms but will not eliminate the problems created by social media or pornography.
Age Attestation vs. Age Verification
Social media and pornography platforms use age attestation to demonstrate compliance with certain laws.REF Age attestation requires users to enter their date of birth or check a box affirming they are over a certain age (13 or older for social media and 18 or older for pornography). Various state and federal laws forbid the selling and distribution of obscene materials to minors.REF However, the high percentage of children under 18 who view pornography illustrates that age attestation is insufficient in blocking online access to kids. The companies do not verify or confirm users’ information for accuracy. Age attestation performs the bare minimum to age-gate users and essentially relies on an honor system.
The Children’s Online Privacy Protection Act (COPPA) of 1998 established regulations regarding commercial website operators’ collection of personal information from children under age 13, such as requiring parental consent. To avoid this special treatment, social media platforms’ terms of service forbid kids under 13 from using the platforms. However, this has done measurably little to keep kids off the platforms. A Common Sense Media report found that 68 percent of children under age 13 use social media.REF An investigation led by New Mexico’s State Attorney General in December 2023 found that Meta had actual knowledge that it had users under the age of 13 but failed to disable or remove the accounts.REF
Legislative efforts to increase the age threshold in COPPA from 13 to 16 have bipartisan support.REF Additional legislation to prohibit kids under 16 from using social media and requiring age verification would provide enforcement teeth. Age-verification methods are not limited to driver’s licenses, as detailed below, but starting the age at 16 means more kids will be able to satisfy the requirement using that method.
Given the harms of social media and encroachment of obscene material on these platforms, raising users’ age strikes a balance with protecting kids and affording parents discretion over their teens’ social media use. Fundamentally, age attestation provides a fig leaf to shield companies from liability, but it does not measurably protect kids.
Device-Level and Platform-Level Age Verification
Age verification confirms the age of a user. It can take place within a device’s operating system, app store, or within a particular platform. Age verification on the device or app store level could reduce the number of times an individual needs to verify his or her age if that user could authorize the operating system or app store to share his or her actual age or coarse age (i.e., user over 13, under 18, over 21, etc.) with a platform. App stores could block downloads of apps with age-ratings higher than the device holder’s age. This would, however, require consistent and reliable age ratings, which app stores currently lack. Age verification at the platform level may still be necessary for multi-user devices such as library and family computers. Additionally, it is necessary for pornography websites that are typically blocked by app stores.
Apple has called for platform-level age verification, claiming that user privacy expectations would be violated if the company was required to share the age of its users with apps. Meta, on the other hand, says that app-by-app age verification is impractical; the company is calling on operating systems or app stores to conduct age verification. It appears neither entity wants to be the responsible, liable party.REF Instead of focusing on determining which method is better, lawmakers should turn their attention to the desired outcome: enforcing age restrictions and consistently preventing kids under a certain age from accessing and creating accounts for platforms not appropriate for their age. The solution may be “both and,” not “either or.”
Existing Age-Verification Technology
Age-verification technology exists and there are variations. Despite its objection to platform-based age-verification requirements, Meta’s subsidiary, Instagram, began testing options in the U.S. for age verification in June 2022. The company prompts age verification for users who attempt to change their birthdate from “under the age of 18” to “18 or older.” The options are uploading a government identification, recording a video selfie, or asking mutual friends to verify their age.
Biometric Verification. Instagram then shares the video selfie with the technology company Yoti to estimate the age of the user based on facial features. Meta and Yoti delete the image upon age verification.REF Data deletion is crucial for mitigating malfeasance from bad actors. Yoti boasts a 99.65 percent true positive rate for 13- to 17-year-olds correctly estimated to be under age 23, and a 98.91 percent true positive rate for six- to 11-year-olds estimated to be under 13.REF
FaceTec is another company that relies on biometrics through face identification in a short video to perform age or ID verification. FaceTec is a software that creates a 3D map of an individual’s face with a two-second video. FaceTec uses anti-spoofing artificial intelligence certified by the National Institute of Science and Technology and the National Voluntary Laboratory Accreditation Program. The software boasts a 1/125,000,000 false acceptance rate and less than 1 percent false rejection rate for its ID matching, and the company will pay a $600,000 bounty to testers who fool the system. The Department of Homeland Security and several international banks are among its users.REF
Direct Input of Personal Information. Online gambling websites such as FanDuel and Draft Kings require users to directly input their personal information on the website for age and identity verification when creating an account. Users must provide their full name, date of birth, phone number, e-mail address, home address, and last four digits of their social security number that the companies then verify. There is little pushback on this method for this use case. Perhaps because gambling inherently requires financial transactions, users expect to provide personal information, whereas because social media and pornography do not necessarily require financial transactions from users, users do not expect to provide the same level of personal information directly with the platform. This latter point underscores the need for multiple options and methods, particularly when it comes to any legislation requiring age verification.
Anonymous Verification. Louisiana was the first state to enforce age verification for pornography websites. Since then, 18 other states have passed similar laws.REF Louisiana sanctioned LA Wallet, a third-party mobile application, as the official digital credential of a state-issued ID such as a driver’s license. Using LA Wallet, pornography websites can anonymously verify the age of website visitors. When someone visits a pornography website, he or she shares only the minimally necessary information the website needs to approve access, which, in this case, is the person’s coarse age.
The website requests a temporary anonymized code, similar to dual-authentication methods commonly used by banks and online merchants, that the user then enters into his or her LA Wallet app. The app notifies the user of information the website needs (again, coarse age), and the user consents before any information is shared. Upon user approval, the app sends the coarse age to the website, and if the user is 18 or older, the website grants the user access. If the user is under 18, then he or she is denied access.REF
Location-Based Verification. Legislative requirements would be strengthened if they include requiring the platforms to take extensive due diligence to determine whether the user is located in the covered jurisdiction beyond the geographical registration of the Internet Protocol (IP) address. One method is to subject known virtual private network (VPN) IP addresses or proxy servers of users to the age-verification measure unless platforms determine with available technology that the user is not located within the jurisdiction.
An IP address is the unique numerical identifier and geolocation of a device connected to the Internet. VPNs can be used to manipulate an IP address to make a device appear as if it is in a different location—often for security and privacy measures—but they may also be exploited by individuals to circumvent age-verification requirements. Subjecting known VPNs to the age-verification process will make circumvention more difficult.REF
Extensive due diligence using available technology includes assessing GPS, cell tower, and wi-fi network data to determine whether the user is located within the jurisdiction. More simply, legislative requirements could prohibit platforms from relying only on the geographical registration of an IP address before determining whether the user is within the jurisdiction. Importantly, this must not allow for tracking users at all times but instead be limited to the specific moment when a user is requested to verify his or her age.REF
Costs. Age verification comes with a cost typically borne by the companies required to comply. The LA Wallet founder said compliance companies pay 10 cents per age challenge.REF Utilizing age verification at the device level may decrease redundancy from piecemeal app-level verification, which could lower overall costs.
However, again, device-level age verification likely would not eliminate all cases for platform-led verification. Complying companies such as Apple, Google, Meta, and Pornhub each generate tens or hundreds of billions of dollars in annual revenue and therefore can more easily absorb costs. Legal requirements for age verification should hold the device-makers, platforms, and websites throughout the chain of access liable and responsible.
Layering Data Privacy and Security Measures
Objections to requiring age verification are typically related to concerns of user privacy. Any legislative requirements for age verification must include data privacy and security measures. Data privacy measures should include defining government-issued identifiers, biometric information, and financial account information, among other things, as sensitive data. Measures must include: (1) limits on whether entities collect data and which data they collect; (2) how long they may retain such data absent immediate deletion; and (3) prohibitions on transferring sensitive data absent consent from the individual.
Data minimization requirements are necessary to ensure any data collection is limited to what is minimally necessary to provide the service (in this case, age verification)—and nothing more. Entities must use security measures to safeguard data against cybersecurity breaches, limit data retention, and require data deletion.
Cultural norms and reluctance to change also feed objections. Requiring age verification may shatter users’ skewed perception of anonymity on the platforms. Websites and apps use cookies, pixels, and IP addresses to track and identify user activity and may share this activity with third parties absent user consent. These platforms compile user analytics, create detailed personalized profiles to provide curated recommendations, and serve personalized advertisements.REF In essence, without robust age verification, platforms still know their users’ identities and ages based on behavioral patterns and Internet activity. Detractors are better served focusing their attention on requiring robust privacy and security regulations.
Limitations of Filters and Blocking Software
Critics also raise questions about whether age-verification requirements are constitutional. The Supreme Court has determined on multiple occasions that the government has a compelling interest to protect children from obscene content.
Judicial History. In Ginsberg v. New York, the Supreme Court determined that the government has a legitimate interest in protecting children from exposure to obscene material and that states could regulate those materials.REF In Reno v. American Civil Liberties Union, the Supreme Court decided that the technology to zone parts of the Internet for adults-only did not exist in a manner that could ensure accuracy and preserve adults’ First Amendment rights. However, the Court again acknowledged the government’s interest in protecting children from harmful material. In the concurring opinion, Justice Sandra Day O’Connor alluded to the promising prospects of future technology for age verification to work in a way that allows for adults-only zoning without infringing the rights of adults.REF
Later, in Ashcroft v. American Civil Liberties Union, the Supreme Court affirmed a lower court’s determination that provisions in the Child Online Privacy Protection Act of 1998 aimed at restricting minors’ access to sexually explicit material on the Internet were overly broad and likely violated the First Amendment. The Court held that blocking and filtering software was the least restrictive means to protect children.
Failures of Filtering Software. The latter two cases seem like setbacks, and opponents and skeptics of age verification certainly point to these cases; however, nearly 30 years since O’Connor wrote her opinion, society has the technological means for age verification, as well as evidence that filtering software is no longer the least restrictive means to protect children.
Research shows children have been exposed to obscene material with filters in place, and in some cases, that filters prevent access to legitimate medical information and drug- and alcohol-prevention material.REF Excessive or ineffective filtering and the lack of user-friendly interfaces deter some parents from using or implementing software—whether it is made available within an app or a third-party provider. Furthermore, filtering software is often limited to obscene content and does nothing to prohibit children under age 13 from creating social media accounts. Parents also bear the brunt of the cost of filtering software, which can cost $10 to $20 per month.REF This will not impede some parents, but this is a luxury for others who may lack the discretionary income.
Lastly, maintaining the position that the discretionary use of filters is the least restrictive means keeps the burden on parents and leaves many gaps in enforcement. Requiring age verification, in which of-age individuals are permitted and underage individuals are prohibited, truly upholds the government’s compelling interest to protect kids.
Free Speech Coalition v. Paxton. Crucially, the Supreme Court heard oral arguments at the start of this year in the Free Speech Coalition v. Paxton case, and the results will impact ongoing efforts nationwide to require online age verification. In Paxton, the trade association for pornography companies claims adults’ First Amendment rights are impeded by Texas’s online age-verification law. The primary question in this case is whether the law must satisfy the “rational basis” legal standard (which is fairly easy to meet), or whether it should be subjected to a “strict scrutiny” standard, which requires a compelling government interest and a narrowly tailored law.
During arguments, the justices acknowledged the limitations and failures of filtering and blocking software, recognized the advancements in age-verification technology, and reaffirmed the government’s role in protecting children from obscenity.REF While the porn industry wants the court to apply strict scrutiny in hopes that the higher standard would lead to the Texas law’s demise, it is possible the court determines the law satisfies even that standard and upholds its implementation.
Recommendations for Congress and States
Congress and individual states should:
- Pass legislation requiring adult websites to conduct age verification to prevent access from kids;REF
- Pass legislation requiring social media websites to conduct age verification to prevent access from kids under 13, at minimum;
- Pass legislation requiring operating system or app store age verification;REF
- Include commercially reasonable methods for age verification;
- Subject known VPNs and proxy IP addresses to the age-verification process, unless the operating system or platform can reasonably determine with available technology that the user is not in the state/country;
- Include reasonable data privacy and security measures to protect users’ sensitive data, including data minimization, retaining data for no longer than is reasonably necessary to verify age or demonstrate compliance, and data deletion;
- Establish an objective age-rating standard to prevent developers from misrepresenting the age suitability of their apps;
- Require parental consent for app store downloads on devices assigned to minors; and
- Authorize state attorneys general, relevant state agencies, and the Federal Trade Commission to enforce the law.
Conclusion
The status quo of using age attestation to determine a user’s age and the discretionary use of filters is not working to keep kids off pornography websites or prevent underage kids from creating social media accounts. Filtering and blocking software is no longer the least restrictive means to achieve the government’s compelling interest to protect children online due to the software’s ineffectiveness and advances in age-verification technology.
Age verification is the only solution that will consistently keep children under age 13—or any older age set by legislators—off social media and all minors off pornography websites. Considering the clear resistance from Big Tech to employ or require age verification, and because the Internet transcends state lines, society ultimately needs federal legislation that requires age verification on the platform and device level. Parents need help now.
As Kara Frederick wrote, legislation and enforcing agencies like the Federal Trade Commission and state attorneys general “wouldn’t be acting in loco parentis, but instead serving as [parents’] force multipliers.”REF Roughly 70 percent of parents say parenting is more difficult today than 20 years ago and that technology and social media are the top two reasons for increased difficulty.REF Installing or switching on filtering software, monitoring screentime, and delaying providing kids with personal devices are all prudent measures to mitigate the harms from social media and pornography—but they lack the full-stop enforcement of age verification. The virtual world has replaced many physical world experiences, for better and worse. Age verification has long existed in the physical world: It must now be applied to the virtual world.
Annie Chestnut Tutor is a Policy Analyst for the Technology Policy Center at The Heritage Foundation.



